
I found this article to be very inviting – “What are passkeys? A cybersecurity researcher explains how you can use your phone to make passwords a thing of the past” https://theconversation.com/what-are-passkeys-a-cybersecurity-researcher-explains-how-you-can-use-your-phone-to-make-passwords-a-thing-of-the-past-196643
Can the password really be made ‘a thing of the past’ by the ‘Passwordless MFA’ like Passkeys, which are presumably made of 3 factors as below?
- PKI – known for decades to be effective to prove the authenticity of a device with a private key embedded in the device. It’s a good tool for device/machine authentication.
- Biometrics – supposed to authenticate the person who holds the PKI-embedded device, when (only when) the user is not falsely rejected by the biometrics
- Pincode – supposed to authenticate the person when (only when) the user is falsely rejected by biometrics (Pincode, which is no more than a numbers-only password, is supposed to not belong to the password when the solution is called a ‘Passwordless’ solution).
The problems that we identify therein are –
1.Meaning of MFA
While it is often called ‘MFA’ because three factors are ostensibly involved, we should call it Quasi-MFA because (2) and (3) are deployed in a two-entrance/in-parallel formation, which only provides the security lower than that of having two factors deployed in a two-layer/in-series formation.
In other words, their quasi-3-factor schemes made of PKI, Biometrics and Pincode provide a security lower than a 2-factor scheme made of PKI and Pincode. When mixed up, it would be spreading the illusion that it offers the security of a truly three-factor scheme.
As such calling it MFA might well be a very dubious act of getting the users to bear an extra cost for biometrics which can only contribute to lowering the security, and getting the users trapped in a false sense of security.
Remark: The security-lowering power of biometrics used with another factor in a multi-entrance formation is illustrated below
and closely examined in this 2-minute video “Biometrics in Cyber Space” https://youtu.be/wuhB5vxKYlg
You may now be well convinced that, if we remove biometrics from such a quasi-MFA of PKI, Biometrics and Pincode, we would have a 2FA of PKI and Pincode that provides a higher security than the quasi-MFA.
2.Private Key of PKI
A private key of PKI embedded in a device is vulnerable to theft and abuse. The risk would be greater if it is copied and stored somewhere physically, whether online or offline.
Well, on the bloated belief in cryptographic certification – “I registered this wallet as mine with the authority so that the authenticity of my wallet is to be proven by a cryptographically-certified tag embedded in the wallet”. Someone utters – “So, with the bless of the might of the authority, whoever holds the wallet should be authoritatively proven to be your esteemed self”.
Should the private key be memorized in a human brain, PKI could be called a good tool for user authentication.
3.Troubles of Pincode
Users of the likes of PassKeys have to continue to struggle with the dilemma of easy-to-remember or easy-to-break pincode. When you anticipate that you do not need a pincode unless you get occasionally rejected by biometrics, would you wish to register a hard-to-recall (generally hard to break) pincode?
Moreover, a pincode, numbers-only password, looks simpler than an alphanumeric password, but looking simpler does not mean that it is easier to remember firmly. It is often easier to confuse as many of us have experienced here and there.
Then, What Can We Offer?
Our PKI solution (tentatively called Mnemonic PKI) for online login that we plan to put on the global market following Mnemonic Gateways password manager (*) will relieve the users of PKI of the concerns about the theft and abuse of the private keys.
Private keys, which are non-existent when not needed, can be regenerated from (only from) the users’ non-volatile image memory.
The burden on the users is just locating several known images, whereas the entropy of the keys generated from the combinations of images could easily exceed millions of bits.
The program (having no secret data in it) can be copied on multiple devices for not losing good availability.
* “Mnemonic Gateways as Leading Digital Identity App” https://www.linkedin.com/pulse/mnemonic-gateways-leading-digital-identity-app-hitoshi-kokumai/
By turning the function of regenerating multiple high-entropy passwords on-the-fly from users’ non-volatile image memory into regenerating multiple private keys of PKI the same way, we will be easily able to achieve what the likes of PassKeys can by no means achieve.
………………………….
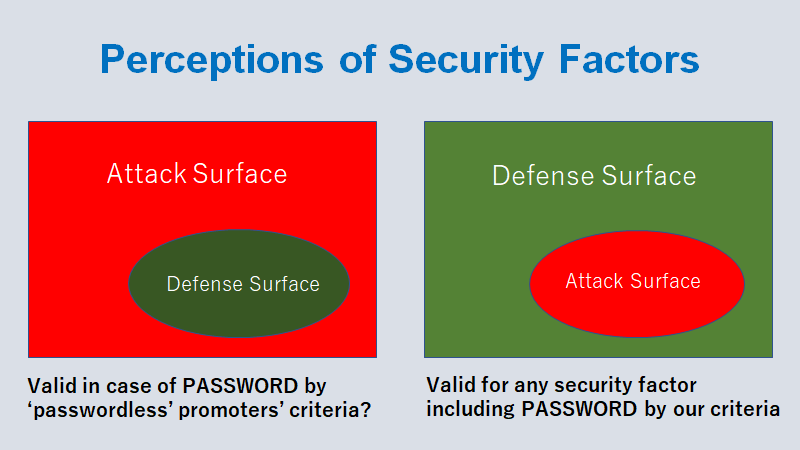
Appendix – What is behind ‘Passwordless’ misperception?
Removal of the password would contribute to a higher identity security where (only where) the password’s attack surface of the password is larger than its defense surface.
1 minus 1 is not larger than 1. Two minus one can never be larger than two. Should we feel anxious that the password alone is not good enough, we should think of adding another factor on top of the password, not removing the password. It is a no brainer, unless we are trapped in a cognitive pitfall.
Here is a closer discussion on this subject – “How to not see our weak digital identity further weakened” https://www.linkedin.com/pulse/how-see-our-weak-digital-identity-further-weakened-hitoshi-kokumai/




 From Imperial Shackles to Sovereign Justice: The Decolonisation Journey of Indian Criminal Laws
From Imperial Shackles to Sovereign Justice: The Decolonisation Journey of Indian Criminal Laws