Humans have become a weak layer of defense at endpoints because they are reacting vs. responding to cyberattacks. They are considered the weakest link in the cybersecurity chain because their nature often leads them to exhibit noncompliant behavior (Goel, 2017 January 18). Reactions can damage the endpoint, compromise the data it accesses, or cause permeation to other computing devices. Cloud-based security awareness training (SAT) can be curated from modules to educate your employees how to identify threats, how to defend themselves, and how to report the threat timely. Threat vectors can be targeted at industries, data, businesses processes, documents, or storage types; those facets should be identified and evaluated to determine which SAT modules should be curated into a training package to educate ALL employees about [information] security awareness.
–
It’s reasonable to deduce that the prevalence of broadband, its increasing speed and bandwidth, and the incremental rollout of 5G cellular networks are making it easier for cyber-attackers to attack remotely without being found. The connectivity benefits of this paradigm shift in broadband Ethernet and fast cellular networks have created a global network of Internet users that follow-the-sun for connectivity (e.g. endpoints, cloud applications, e-commerce). Cyber attackers have engineered ways to exploit vulnerable endpoints anonymously via botnets or via [stealthy and fraudulent] social engineering; their goal is information theft, espionage (steal information), sabotage, steal assets to resell, or generate cash (Trend Micro, 2015 October 22). The global reach of these threats, and their frequency, have existed for less than 15 years (e.g. circa 2005), yet users are just beginning to learn to defend themselves from them. The fortification of networks, email, and cloud have prompted attackers to expand use of social engineering to acquire resalable assets or cash. Cyberattacks are occurring more frequently, prompting the need for quality security awareness training (SAT) for all classes of employees (e.g. board member to line worker) that should be delivered more than one time per year. SAT was historically an unwanted chore, operational expense, and failed to be effective. However, SAT endeavors to transform computing and defense behavior to block attackers more frequently from achieving their goals. The National Cybersecurity Institute makes a good point, “Without training, workers will likely lack the skills and knowledge they need to adequately protect their companies’ networks from cyberattacks” (Baier, 2012 October 5). Cyber situational awareness is the key to minimizing the effect of human error on an organization’s cybersecurity posture (Goel, 2017 January 18). SAT can prepare all employees of the enterprise to recognize a cyberattack, defend themselves from it, and report it timely.
–
Humaidi & Balakrishnan (2015) found that transactional leadership is more likely to be successful than transformational leadership. It’s reasonable to deduce from their findings that employees avert changes to their successful work habits, yet welcome recognition for successes. If the threat surface of the computing environment is to shrink, its human layer must remain educated to identify threats and be trained to respond vs. react to them. To reach that goal, employees must attach value to change their behavior via a defined process of self-defense. Transformational leadership of cybersecurity is positioned to occur when executives and stakeholders plan defense layers. Selection, procurement, and creation of SAT that meets the risk management needs of the enterprise can be accomplished through a security council or steering committee made up of C-level executives, stakeholders, and asset owners. The existence of the security council and the relationships with the other committees should be embedded in the SAT for every end user within the organization (Fitzgerald, Krause, 2008). If SAT is to contribute to risk management successes, it must be planned by management with transformation of behavior in mind. Adoption of an innovative solution is likely if recipients place value on it; an implementation plan and leadership should be designed to help recipients recognize that value for themselves. Therefore, events of successful defense from SAT should be recognized within the company intranet. Recognition of defense will encourage other employees to contribute to human defense, organic expansion will likely follow. It’s noteworthy that planning for and deploying SAT is a subtle example of innovating behavior and aiding its adoption through adaptive leadership (Cambridge, n.d.). Security awareness by end-users of all types, will increase and mature to leverage human interaction as a strong defense shield against a cyberattack, becoming part of the security stack serving the network.
–
Transforming employee behavior requires identifying and addressing risk exposures that are most likely to impact the organization (Wheeler, 2011, 287). Modules within SAT programs can be curated to explain those risks, how to identify them, and how to respond to them. The curation of specific education modules within SAT programming can endeavor to transform the behavior of employees regarding physical and technical security events (e.g. some form of unauthorized access, reporting unusual computer activity, or defending themselves from a social engineering attack). Deployed SAT will educate employees regarding real threats and weakness, enabling them to become a human layer of security risk management capable of responding with procedures vs. reacting to unknown threats as a victim (Wheeler, 2011, 287). Help employees make the right decisions when face-to-face with a wide range of cybersecurity risks, from phishing attacks to insider threats (Proofpoint, n.d.)
–
Current versions of SAT educates all workers to maintain secure hygiene habits, to defend themselves from attack, and to report cyber events to the helpdesk timely. The key to delivering effective SAT is to ensure that all staff access it, as vulnerabilities may lie where least expected (Caldwell, 2016, Jun). A variety of 3rd-party vendors such as ELC Information Security offer security awareness training via the Internet or on-prem software (ELC IS, n.d.). Proofpoint is also recognized as an effective cloud-based provider; frequency is recommended twice per year to maintain current about threat variants (Proofpoint, n.d.). SAT can be fostered and encouraged through an internal marketing plan of blog posts on the company intranet, email broadcasts, and wall signage. That marketing effort helps all classes of staff to accept the need to remain current on security threats, and how to deal with them second-nature.
–
References
–
Goel, A. (2017, January 18). Securing Human Endpoints Through Cyber Situational Awareness, Security Intelligence, Retrieved from https://securityintelligence.com/securing-human-endpoints-through-cyber-situational-awareness/
–
Trend Micro (2015 October 22). Understanding Targeted Attacks: Goals and Motives, Trend Micro, Retrieved from https://www.trendmicro.com/vinfo/us/security/news/cyber-attacks/understanding-targeted-attacks-goals-and-motives
–
Baier, E. (2015 October 5). Employees Are First Line of Defense for Cyber-Attacks, Digicert, Retrieved from https://www.digicert.com/blog/employees-are-first-line-defense-for-cyber-attacks/
–
Humaidi, N., & Balakrishnan, V. (2015). Leadership styles and information security compliance behavior: The mediator effect of information security awareness. International Journal of Information and Education Technology, 5(4), 311–318. Retrieved from http://www.ijiet.org/papers/522-I00016.pdf
–
Fitzgerald, T. & Krause, M. (2008). CISO Leadership: Essential Principles for Success, Ch. 14, Auerbach Publications.
–
Cambridge (No Date). Adaptive Leadership, What is Adaptive Leadership?, Cambridge Leadership Associates, Retrieved from: http://cambridge-leadership.com/ adaptive-leadership/
–
Wheeler, E. (2011). Security Risk Management, c. 14, p. 287, Elsevier
–
Proofpoint (No Date). Proofpoint, ProofPoint, Retrieved from https://www.proofpoint.com/us
–
Caldwell, T. (2016, Jun). Making security awareness training work, Science Direct, Retrieved from https://www-sciencedirect-com.library.capella.edu/ science/article/pii/S1361372315300464
–
ELC IS (No Date). Make Security Awareness Training, ELC Information Security, Retrieved from https://www.elcinfosec.com/security-awareness-training-for-employees



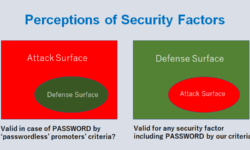

 Existential Risk Analysis (ERA) – The Basics
Existential Risk Analysis (ERA) – The Basics