 Many of the recent cyber-centric innovations, which some people call ‘techceleration’, would end up with pipedream without solid identity assurance,
Many of the recent cyber-centric innovations, which some people call ‘techceleration’, would end up with pipedream without solid identity assurance,
Conventional text-passwords are obviously unable to meet the need, but it does not mean that ‘password-dependent password-less authentication’ and ‘password-dependent password-killer biometrics’ are valid solutions. These delusive concepts would only bring catastrophic disasters to security and democracy.
In the post-pandemic techceleration age do we desperately need ever more reliable identity assurance. Can we afford to continue to think light of the potential of ‘non-text’ secret credentials?
Prerequisite for Solid Digital Identity
Shall we start from these observations? – No safe and orderly societal life would exist without solid identity assurance.
No solid identity assurance would exist without solid secret credential for identity authentication, whereas the text-password as a conventional secret credential is no longer manageable.
Then, we will naturally get to the observation that we could and should look to ‘Non-Text’ secret credential as illustrated below.
Impacts that Episodic Memory Has on Digital Identity
Our own episodic memory plays a big role in multiple aspects; it actually enables us to
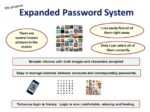
come up with Expanded Password System as a legitimate successor to text passwords,
“Digital Identity for Global Citizens” (90-second video)
convert a set of unforgettable images to a high-entropy complex password,
“Image-to-Code Conversion by Expanded Password System”
regenerate the seed of symmetric and asymmetric cryptographic keys on-the-fly,
“Account Recovery with Expanded Password System”
thwart nasty phishing attacks effectively,
“Detection of Phishing by Episodic Image Memory”
mitigate onerous insiders’ jobs and other persistent attacks,
“Advanced Persistent Threats in Digital Identity”
and design a new breed of Brain-to-Machine Interface.
“Password & BCI/BMI (Brain-Computer/Machine-Interface)”
Citizens in an inclusive society must be able to demand that their volition be confirmed when their digital identity needs to be authenticated for their civic rights and duties. ‘Identity Assurance by Our Own Volition and Memory’, our principle, could well be a fundamental requirement of democracy.
Incidentally, a typical definition of Episodic Memory is “the ability to recall and mentally reexperience specific episodes from one’s personal past and is contrasted with semantic memory that includes memory for generic, context-free knowledge.”
https://www.sciencedirect.com/topics/neuroscience/episodic-memory
‘Hard-to-forget’ secret credentials are made feasible by the intrinsic nature of the emotion-colored ‘episodic memory’; When we register, as our secret credential, the pictures of our episodic memory that have survived in our brain for decades, do you think that we can get them forgotten over the next few years or so (assuming we are fit for societal life)?
What are certain about authenticators
We are often asked to confirm that Expanded Password System (EPS) that we advocate is more secure and user-friendly than text password, physical token and biometrics. Our answer is “It is unknowable. It’s in the sphere of agnosticism”.
A very poorly designed, implemented and operated EPS could possibly be less secure and less user-friendly than other solutions that are wisely designed, implemented and operated. (Certainly, we have the knowhow to have EPS wisely designed, implemented and operated thanks to very demanding clients.)
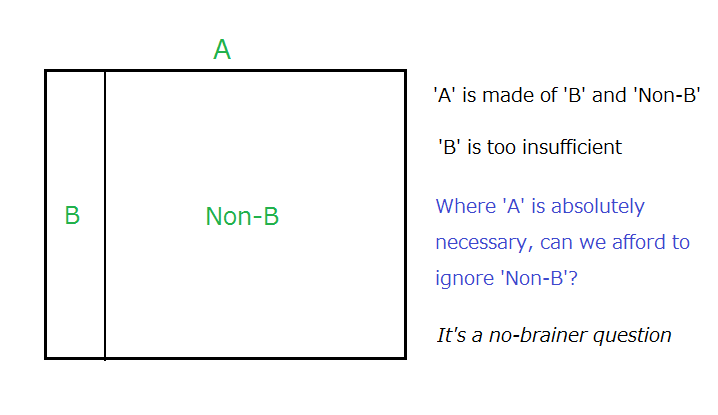
Besides that, what is known to us for certain by logic about various authenticators are
A: ‘Yes/No’ on feeding correct passwords/EPS and ‘Yes/No’ on presenting correct tokens are deterministic, whereas biometrics which measures unpredictably variable body features of living animals in changing environments is probabilistic.
B: It is practically impossible to compare the security of a strong or silly password with that of a poorly or wisely deployed physical token even though both passwords and tokens are deterministic,
C: Direct comparison of something deterministic and something probabilistic would absolutely bring us nowhere.
D: Deterministic authenticators can be used on its own, whereas a probabilistic authenticator would lose its availability when used on its own.
E: Deterministic authenticators can be used together in a security-enhancing ‘multi-layer’ deployment, whereas probabilistic authenticators can be used with another authenticator only in a security-lowering ‘multi-entrance’ deployment unless we can forget the availability.
F: Removal of the password brings a catastrophic loss of security. It also makes a grave threat to democracy.
G: PIN belongs to the family of password as a numbers-only password; displacing a password by a PIN is like displacing a ‘knife’ by a ‘paper knife’.
H: Password/EPS, tokens and biometrics are ‘authenticators’, while two/multi-factor schemes, decentralized/distributed digital identity, single-sign-on schemes and password management tools are all ‘deployment of authenticators’; We would obtain nothing by comparing the former with the latter.
Takeaways from Expanded Password System Development
How we built it – The system is built to enable the user to register a set of any numbers of images of their choice either by permutation or combination as credentials and embed them onto a matrix of images made of meaningless decoy images.
Challenges we ran into – However solid the theory is, the solution would be vulnerable to attacks when it is poorly implemented. A key was the appropriate use of a hash module of SHA family.
It was also a challenge to get technology people to listen to us about the merit of making use of our own autobiographic/episodic memory. These people are generally not familiar with such psychological concepts.
Accomplishments that we’re proud of – Adoption by demanding clients such as Japan’s Ground Self-Defense Force (Army) besides the use cases in consumer and corporation areas.
Also, selection as a finalist by Financial Data and Technology Association for ‘Summit and Awards 2019’ and adoption by AFCEA for ‘2020 Solution Review Problem Sets’.
What we learned – Our solution can and must be made available to global citizens.
We also learned that, for global citizens to enjoy a safer identity assurance, we need to debunk wide-spread misperceptions such as “indispensable passwords be removed altogether” and “passwords be displaced by password-dependent biometrics”
What’s next – Global operations
The theory behind our solution is the science of Human Memory, especially episodic memory that had been acquired long time ago, solidly inscribed deep in our brain and are expected to stay further for many more years. Our philosophy of digital identity is ‘Identity Assurance by Our Own Volition and Memory’. This is quintessential in the society where the values of democracy are respected.
Incidentally, Expanded Password System is to be found on the layer of ‘authenticator’, while the likes of Open ID and FIDO are all to be found on the upper layer of ‘deployment of authenticators’ and, as such, the likes of Open ID and FIDO could naturally be our down-stream partners.
Launching Global Operation
Our history of promoting the digital identity principle of ‘Identity Assurance by Our Own Volition and Memory’ started in 2001 in Japan where we set up Mnemonic Security, Inc. as the first company to provide the software products for Expanded Password System (EPS) that accepts images of episodic memory as well as conventional texts, which is intended to be a legitimate successor to the time-honored seals, autographs and text-only password systems.
Our EPS software and applied solutions offer ‘Hard-to-Forget’, ‘Hard-to-Break’ and ‘Panic-Proof’ digital identity authentication. The software can be used stand-alone, as the master-password of password-managers and single-sign-on services, as a factor of multi-factor authentication schemes and as a fallback measure of biometrics.
Now, we registered Mnemonic Identity Solutions (MIS) Limited (Code: 12788178) in UK as our global headquarters in August 2020 for promoting EPS worldwide. We will be starting the active operation as soon as the current pandemic has substantially subsided.
The aim of our enterprise is to make EPS solutions readily available to all the global citizens: rich and poor, young and old, healthy and disabled, literate and illiterate, in peace and in disasters.
We expect EPS to stay with us over many generations until humans discover something other than the ‘digital identity’ for our safe and orderly societal life. We look for the people who share such a long-term view and support us as such.
Although we have years of experiences with military, corporate and consumer adoptions in Japan, we are a sheer start-up in view of launching the global operations. We are short of all the kinds of business resources for it. We will welcome any help and support in any aspect of our worldwide business activities.
Hitoshi Kokumai
Managing Director, Mnemonic Identity Solutions Limited
Profile: Hitoshi kokumai is an advocate of ‘Identity Assurance by Our Own Volition and Memory’ and the inventor of Expanded Password System that enables people to make use of episodic image memories for intuitive and secure identity authentication. Besides that, he has kept raising the issue of wrong usage of biometrics and the false sense of security it brings for 20 years.
——————————————
Appendix – What we could do for NOT achieving solid digital identity
Follow the arguments that promote ‘passwordless authentication’ or ‘password-dependent password-less authentication’ and we would be successful in not achieving solid digital identity.
Should ‘passwordless’ literally mean ‘removal of all the password family’, we would be actually watching the ‘passwordless authentication that is quite like an ATM that does not ask for your PIN in dispensing your money.
Should a PIN, that is a numbers-only weak password, be used in the passwordless authentication, we would be watching the delusive ‘password-dependent password-less authentication’,
Either of them would infallibly take us away from solid digital identity.
Incidentally, biometrics, which requires a default/fallback password/PIN, naturally is not qualified to claim to sustain the ‘passwordless’ authentication.
Who says that passwords are bad?
Some people allege that passwords must be removed from digital identity because they are bad.
We can agree that passwords are not secure – they can be lost, stolen and abused. Well, we can also agree that physical tokens are not secure – they can be lost, stolen and abused.
What puzzles us is the argument of ‘passwordless’ people that the password should therefore be removed while the physical token should therefore be relied upon. We feel like falling into a Rabbit Hole.
Unbelievable Power of PIN
We hear that there are people who do not view the PIN as a member of the password family and allege that the PIN tied/linked to a hardware is more secure than the password not tied/linked to a hardware. It might sound superb to some people, but we wonder what we would see if someone starts linking the password to the same hardware.
This PIN story could be compared to a paper knife tied to the tip of a long stick, which may well be more fatal than a knife on its own in a certain situation. But what if we get the knife tied to the tip of the same stick in the same situation? In a Rabbit Hole again?
Incidentally, where a biometrics sensor is also tied/linked to a hardware together with a PIN in a multi-entrance deployment (as against a multi-layer deployment), the overall security is made even lower than a PIN-only login. It’s no good for the glorious PIN.
All those funny phenomena might have come from a simple mistake of mixing up something ‘insufficient’ with something ‘harmful’.
In a parallel world, because it is so vulnerable to air attacks, the ground force should be removed from the defense system for better national security. “Being vulnerable is bad. Bad things should be removed.”
In that parallel word, the lock/key system should also be removed from home security, because keys are lost, stolen and abused. With the lock/key system removed, people would no longer have to worry about the loss, stealth and abuse of their home keys.
Where ‘army-less’ national defense and ‘lock/key-less’ home security are both valid, ‘password-less’ authentication’ must naturally be valid, without question.
Well, these funny scenes might also be the result of confusing the discussion of ‘authenticators’ with that of ‘deployment of authenticators.’
Mixing up ‘Deployment of Authenticators’ with ‘Authenticators’
There are not a few security professionals who wrongly mix up the layer of ‘authenticators’ with that of ‘deployment of authenticators’, talking as though the former and the latter were competing each other, for example, ‘Multi-Factor Authentication is better than the password authentication’ and ‘ID federation is better than a password login’
The password is an ‘authenticator’. So are the token and biometrics. Whereas two/multi-factor authentications, ID federations, self-sovereign identity and all the cryptographic identity schemes are all ‘deployment of the authenticators’
What we find behind Convenience of Biometrics
As a very convenient tool to achieve the ‘passwordless’ authentication, biometrics is often loudly touted by a number of global big names.
Nothing looks more convenient than putting your finger on a sensor or place your phone in front of your face to get you logged-in. Is it actually as convenient?
Consider the huge inconvenience that citizens would have to face over their lifespan when their biometrics data, that cannot be cancelled, have been leaked.
Consider another big inconvenience that citizens would have to face when their default/fallback text-password/PIN, to which most people pay little attention about security, has been broken.
Very sadly, not only consumers but quite a few security professionals are unconscious of the fact that biometrics used in cyberspace does not make an additional layer, but provides an additional entrance like a backdoor as you find in the picture below.




 Ensuring Water Safety, Security, and Sustainability
Ensuring Water Safety, Security, and Sustainability