Prof. (Dr.) Sérgio Tenreiro de Magalhães, an Associate Professor and Chair of Cybersecurity at Champlain College Online based in the United States, participates in Risk Roundup to discuss a Machine Learning Approach to Keystroke Dynamics based User Authentication.
A Machine Learning Approach to Keystroke Dynamics-Based User Authentication
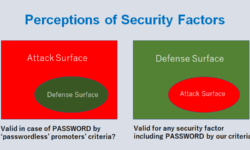
Over the years, nations’ traditional approach to cybersecurity has been the use of passwords and password-based authentication. Passwords have undoubtedly provided cyberspace-based digital systems and platforms with a not so strong barrier to accessing what was quite safe in the analog world so far. However, since the digital age and the advances in computing provided the means to quickly try hundreds of thousands of passwords in a short time, the password-based authentication system is no longer considered safe and secure.
Since hacking passwords have become relatively simple, it is no surprise that we need the effectiveness of strong authentication systems for digital identity and age. Understandably, a new approach to identity authentication has become essential.
Current State
The majority of computer systems across nations today employ a login ID and password as the principal method for access security. It needs to be understood that, in stand-alone situations, this level of protection may be adequate. However, when computers are connected to the internet, the vulnerability to a security breach is increased enormously.
Since it is becoming clear that we need more reliable processes of authentication, it is essential to evaluate the common authentication solutions used today:
- What are the common authentication solutions?
- Will any alternative to text-based password, for instance, graphical passwords, can enhance the level of security of trusted computer systems?
- In the context of Information Systems (IS), what does authentication involve?
- What kind of biometric solutions are emerging?
- Which class of biometrics will provide a high level of security?
Keystroke Dynamics
Keystroke dynamics is a behavioral biometric that is based on how a user enters their login details. This collection of attributes is then used to form a reference signature, a biometrics identification record that can be used for subsequent authentication requests.
The core of the keystroke dynamics is the typing style of a user, the typing style that includes such factors as the length of time it takes to type the login id/password, how long each individual depresses a key, and how long it takes to type successive keys. By collecting all these data– it is possible to develop a model of how the person types. Since this is not a one-time exercise, in addition to this static information, a person’s typing style evolves with continued practice and usage and can be adequately quantified.
Since keystroke-based behavior biometrics is not a one-time collection of behavioral biometric data, it is critical to evaluate whether the ongoing need for exercise creates any opening for manipulation and other vulnerabilities.
- How is the data collected for behavioral-based biometrics?
- Once the keystroke data has been collected, how is the reference signature obtained for users?
- How is the profile of a user-built?
- Where are the research efforts headed to keystroke dynamics authentication algorithms?
- Since the user identification and authentication are significant security concerns on all kind of computational systems, how will the improved statistical keystroke dynamics algorithm resolve user identification and authentication problem?
- What is the precision of keystroke-based authentication technology?
- What is the processing capability of the keystroke algorithm?
- How would the keystroke system prevent illegitimate login attempts?
- On what devices can this keystroke biometry be used?
- What protocols need to be followed for developing a web-based application with an authentication system based on static keystroke dynamics?
- What does keystroke authentication involve?
- What is the machine learning approach to keystroke dynamics?
- Will the keystroke technology be feasible for large scale implementation?
- Is this technology sufficient to be a stand-alone authentication technology?
- What technical/non-technical challenges still need to be resolved before the keystroke technology can be applied commercially?
The time is now to begin a discussion on all these questions and more as we start to evaluate a machine learning approach to keystroke dynamics-based authentication solutions.
For more, please watch the Risk Roundup Webcast or hear the Risk Roundup Podcast
About the Guest
Dr. Sérgio Tenreiro de Magalhães is an Associate Professor and Chair of Cybersecurity at Champlain College Online. He has taught courses in a range of information security disciplines internationally for over a decade.
Dr. Tenreiro de Magalhães is a member and reviewer of a number of organizations, including the NATO Multinational Cyber Defense Education and Training project and the Editorial Committee of the International Journal of Electronic Security and Digital Forensics. His research interests focus on information security, intelligence, and performance monitoring. His research on security-related topics is widely published.
About the Host of Risk Roundup
Jayshree Pandya (née Bhatt), Ph.D., is a leading expert at the intersection of science, technology, and security and is the Founder and Chief Executive Officer of Risk Group LLC. She has been involved in a wide range of research, spanning security of and from science and technology domains. Her work is currently focused on understanding how converging technologies and their interconnectivity across cyberspace, aquaspace, geospace, and space (CAGS), as well as individuals and entities across nations: their governments, industries, organizations, and academia (NGIOA), create survival, security, and sustainability risks. This research is pursued to provide strategic security solutions for the future of humanity. From the National Science Foundation to organizations from across the United States, Europe, and Asia, Dr. Pandya is an invited speaker on emerging technologies, technology transformation, digital disruption, and strategic security risks. Her work has contributed to more than 100 publications in the areas of science and commerce. She is the author of the books, Geopolitics of Cybersecurity and The Global Age. She writes about Artificial Intelligence on Forbes.
About Risk Roundup
Risk Roundup, a global initiative launched by Risk Group, is a security risk reporting for risks emerging from existing and emerging technologies, technology convergence, and transformation happening across cyberspace, aquaspace, geospace, and space. Risk Roundup is released in both audio (Podcast) and video (Webcast) format. It is available for subscription at (Risk Group Website, iTunes, Google Play, Stitcher Radio, Android, and Risk Group Professional Social Media).
About Risk Group
Risk Group is a Strategic Security Risk Research Platform and Community. Risk Group’s Strategic Security Community and Ecosystem is the first and only cross-disciplinary and collective community that is made of top scientists, security professionals, thought leaders, entrepreneurs, philanthropists, policymakers, and academic institutions from across nations collaborating to research, review, rate and report strategic security risks to protect the future of humanity.
Copyright Risk Group LLC. All Rights Reserved




 Learning In Autonomous Systems
Learning In Autonomous Systems